In ESP RainMaker, all node-cloud communication happens over MQTT. However, recently we've announced support for this communication to happen over HTTPS. This is enabled using Mutual TLS. This requires two-way authentication between the client and the server. With mutual TLS, clients must present X.509 certificates to verify their identity to access APIs.
Before going ahead, decide what domain name you want the nodes to use for connecting. For example, api.node.rainmaker.espressif.com. Let's call this the node endpoint.
Pre-requisites
To enable mutual TLS, you need to create a custom domain name for the node endpoint. You must have a registered internet domain name to set this up. If needed, you can register an internet domain using Amazon Route 53 or a third-party domain registrar of your choice. An API's custom domain name can be the name of a subdomain or the root domain (also known as "zone apex") of a registered internet domain.
You must have an SSL/TLS certificate ready in AWS Certificate Manager for the node endpoint. For detailed steps refer - Getting certificates ready in AWS Certificate Manager
Steps
- For mutual TLS to work, all CA certificates of the node certificates need to be registered in RainMaker. You might have used [RainMaker Admin CLI]({{< ref "admin_cli" >}}) to register nodes.
- Get the CA certificate at:
<outdir>/<current_date>/Mfg-<no>/common/ca.crt - Convert it from a multi-line string to a single-line string by replacing line breaks with \n.
- Login to RainMaker using the Login API
- Call the Upload Node CA certificate API with the node CA certificate string
Note: If you had registered nodes in multiple batches, you will have to repeat the above step for each batch.
- Call the Configure service API with
service: node_apis
registered_domain_name: the node endpoint domain name
certificate_arn: the ACM certificate ARN of the node endpoint you registered in the pre-requisites
Note the api_gateway_custom_domain received in the API response
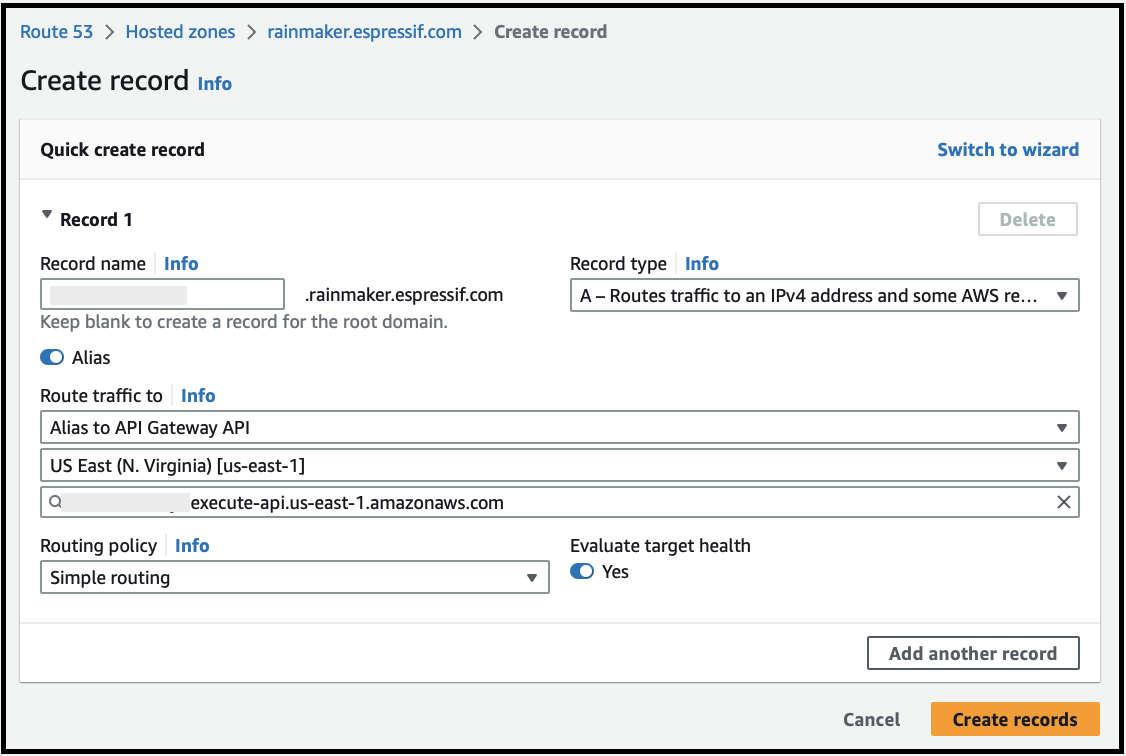
You must now create or update your DNS provider's resource record to map your node endpoint to the api_gateway_custom_domain received in step 2.
In case you are using Amazon Route 53 as the DNS provider, you can create an Alias A record in your hostedzone for the same as shown below:
Node APIs are now enabled for all node certificates registered. You can repeat step 1 if you have a new CA certificate that needs to be registered.
To call the APIs, nodes now need to present a trusted X.509 certificate and possess the corresponding private key. Refer the Node APIs to check the supported node APIs.